Background
I’ve been developing my language (Squeak) for a while now, and have been creating a shellcode agent in it. Initially Squeak was created to explore shellcode and how it is made. It also stems from a little place of jaded perspective.
In my adventures thus far, when C2 agents create a ‘shellcode binary blob’ for C2 operators to implement in their payloads, it seems that most every C2 exports a stub that mounts a DLL or maps an executable. This behaviour results in predictable API calls (which is somewhat unavoidable regardless) and highly signatured payload content, regardless of the underlying encryption/decryption steps.
When I was beginning my adventures in this field, I was under the impression that C2 agents with ‘shellcode’ outputs were full ports of the agent to fully position independent code. Alas, they seems to be fully assembled and linked binaries with a stub to mount them.
King
King is a C2 agent I am currently developing that is compiled to a low entropy (~0.48-0.60), deterministically random blob that does not require encryption to be written to the disk in order to bypass static detection (if that ever changes I will be highly impressed).
Presently, King is being developed to be delivered with Mythic.
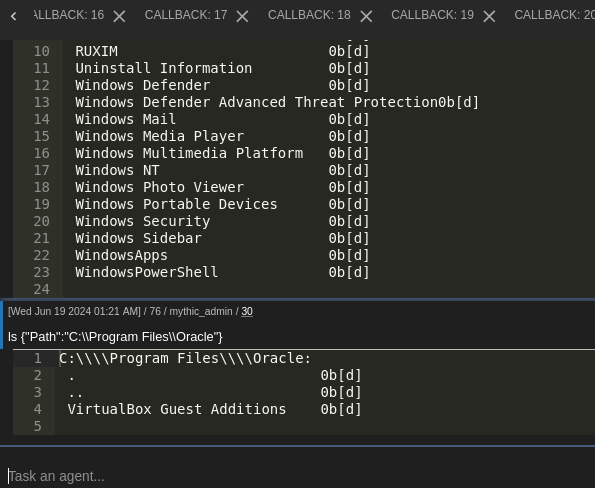
King is not really intended to be a fully fledged C2, at least, not yet. The main functionality or vision for King is to provide a very hard to signature initial access beacon or synchronous shell wrapper. Ideally, you have a victim run the King shellcode and receive a callback. From here, you can install persistence using King and then ‘upgrade’ the King implant to fully fledged C2 beacon for the additional features. This way the secondary C2 beacon should never be written to the disk.
The goal of King really is just to have a completely unknown foothold into an environment using truly unique binary blob instructions. The currently full set of King features planned are:
- cd, ls, mv, cp
- download/upload
- shellcode exec
- shellcode inject
- shellExec/Run
- Reg Read/Write
- PS|Service|Handle enumeration
- Scheduled task creation
The expanded feature set expected for a later release will include:
- AD LDAP enumeration
Since King largely function as a C2 as a shellcode loader, it natively allows for an operator to compile a Squeak shellcode and push it to the agent similar to a BOF in other C2 frameworks.
Leave a Reply